Using the Linux Remote System | (SSH)
What is the remote system?
Remote support makes use of remote access (or distant desktop) software to provide technicians with quick access to a remote device from any location at any time. This means they can give remote support without having to physically visit the equipment.
How to Access Remote Linux Desktop?
There are two different way to connect with your Linux machine remotely
1. RDP (Remote Desktop Protocol)
2. SSH shell (Secure Shell)
Remote Desktop Protocol(RDP):
Remote Desktop Protocol(RDP) is a Microsoft-developed proprietary protocol that allows a user to connect to another computer through a network connection using a graphical interface. RDP servers are included with Windows operating systems, and there is also an RDP server for Unix and OS X.
Secure Shell:

ssh stands for “Secure Shell”.
It is a protocol used to securely connect to a remote server/system. ssh is secure in the sense that it transfers the data in encrypted form between the host and the client.
It transfers inputs from the client to the host and relays back the output. ssh runs at TCP/IP port 22.
The ssh command is made up of three parts:
· ssh command instructs the system to establish an encrypted secure connection with the host machine.
· user_name represents the account that is being accessed on the host.
· host refers to the machine which can be a computer or a router that is being accessed. It can be an IP address (e.g. 192.168.1.24) or domain name(e.g. www.domainname.com).
Secure Shell capabilities:
Functions that SSH enables include the following:
· Users can gain secure remote access to SSH-enabled network systems or devices, as well as automate activities.
· secure and interactive file transfer sessions
· automated and secured file transfers;
· secure issuance of commands on remote devices or systems
· secure management of network infrastructure components.
Why ssh for the remote system.
· The essential tool to master the Linux system administration is SSH, SSH is well known as Secure Shell.
· This is a protocol that is used to securely log in to remote systems.
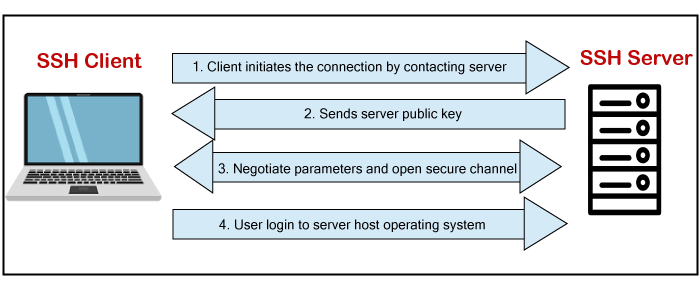
How SSH works?
To make an SSH connection, we'll need two things: a client and a host, which may be anything from a server to a domain name to an IP address. In order to connect to another computer or server, we also need an ssh client. The client establishes the connection using the requested host information, and if the provided credential is validated, it establishes an encrypted connection.
Comments
Post a Comment